Generated by a Log Source, a log message is a data record from a Log Source. Configured in the properties of a Manager (see Configuring a Collector), a Collector is a module that either actively gathers or passively listens for log messages from a type of Log Source. To communicate with Log Sources, each Collector employs an appropriate protocol. For example, a Cisco IDS Collector uses the SDEE protocol to gather log messages from Cisco devices.
For a description of each type of Collector in TLC, along with the protocols and communication port(s) used by each Collector, see Table 27.
|
Type |
Protocol and Required Ports |
Description |
|---|---|---|
|
SSL: TCP/5670 |
If an Agent is installed on a Windows or Linux system, this Collector may be used to gather log messages from any log-generating application running on the host system. Note: To install an Agent, see Installing the Agent Using a Pre-Shared Key. For supported platforms, see Getting Started with the Agent. |
|
|
SSL: TCP/5670 |
If an Agent is installed on a Windows system, this Collector may be used to gather the system's Windows Event Logs. Note: See also the description for the Advanced File Collector. |
|
|
OPSEC and LEA: TCP/18184; UDP/18184 |
Listens for log messages from a Check Point Manager. Note: A Check Point Collector can only collect log messages from a single Check Point Manager. If your TLC environment includes multiple Check Point Managers, then a different Check Point Collector (and, therefore, TLC Manager) must be configured for each Check Point Manager in your environment. |
|
|
SDEE: TCP/443 |
Gathers log messages from Cisco IDS sensors. |
|
|
MySQL: TCP/3306 MS-SQL: TCP/1433 PostgreSQL: TCP/5432 |
Gathers log messages from an application that logs to an External Database. For a list of supported applications, see: http://www.tripwire.com/it-security-software/tripwire-log-center/system-requirements/ |
|
|
SMB: TCP/135-139; TCP/445 SFTP: TCP/22 FTP: TCP/21 |
Gathers or receives log messages from Log Sources that store messages in an ASCII log file. Note: TLC can also collect compressed .zip and .tar.gz log files. |
|
|
Syslog: UDP/514; TCP/1468 SNMP: TCP/162; UDP/162 |
Listens for Syslog and SNMP-based messages from network devices. |
|
|
TCP/IP: 1521 |
Gathers log messages from Oracle database audit logs. For a list of supported Oracle versions, see: http://www.tripwire.com/it-security-software/tripwire-log-center/system-requirements/ |
|
|
WMI: TCP/135, TCP/1024-65535 |
Gathers log messages from Windows Event Logs. Tip: For the collection of log messages from Windows Event Logs, Tripwire recommends the use of the Advanced Windows Collector, rather than the WinLog Collector. |
To collect log messages from a Log Source, you must configure the Log Source to send log messages to TLC (see Appendix I: Log-Source Configuration). In addition, you must create and configure an Asset for the Log Source (see Working with Assets).
|
Note |
When Agent software is installed and configured on a host system (see Installing the Agent Using a Pre-Shared Key), the Agent notifies its TLC Manager, and TLC creates a new Asset for the Agent. For further details, see How does Auto-Discovery work?. |
|---|
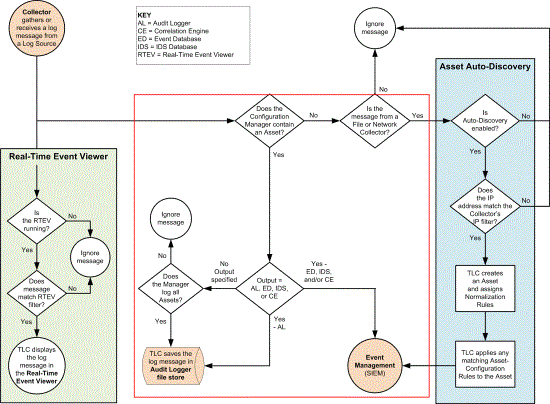
Figure 30 shows how TLC processes a log message collected from a Log Source. Upon receipt of a log message, TLC forwards the message to the Real-Time Event Viewer (see What is the Real-Time Event Viewer?). In addition, TLC determines if:
The message should be stored in the Audit Logger File Store (see What is the Audit Logger?),
The Auto-Discovery process should be started (see Auto-Discovery of an Asset other than an Agent), and
The message should be forwarded to the Normalization Engine (see How does Log-Message Normalization work?).
The steps below describe this decision-making process (outlined in red in Figure 30).
|
Note |
If the Log unknown hosts setting is enabled in the Audit Logger tab of the Manager’s properties dialog (see Working with Managers), TLC saves the message in the Audit Logger File Store regardless of any other steps taken (see What is the Audit Logger?). |
|---|
Figure 30. Collecting a log message
Does the Configuration Manager contain an Asset?
Yes = If the TLC Configuration Manager contains an Asset for the Log Source that generated the log message, TLC refers to the Output Destinations tab of the Asset’s properties dialog.
No = Otherwise, TLC determines what type of Collector collected the message.
Is the message from a File or Network Collector?
Yes = If the log message was collected by a File Collector or Network Collector, TLC initiates the Auto-Discovery process (see Auto-Discovery of an Asset other than an Agent).
No = Otherwise, TLC ignores the log message.
Output = AL, ED, IDS, or CE?
Yes - AL= If the Audit Logger is enabled in the Asset's Output Destinations tab, TLC saves the message in the Audit Logger File Store.
|
Note |
If a message contains the string specified by the Quick Match field in a Normalization Rule (see Table 84), and the message's Collector is assigned to the rule, TLC associates the message with any Classification Tags assigned to the rule when the Audit Logger indexes the message. For more information, see How does Classification work?. |
|---|
Yes - ED, IDS, and/or CE= If an Event Database, IDS Database, and/or Correlation Engine is enabled in the Asset's Output Destinations tab, TLC sends the log message to the Manager's Normalization Engine (see How does Log-Message Normalization work?).
No Output specified= If no Output Destinations are enabled for the Asset, TLC refers to the Log all Assets setting in the Manager's Audit Logger tab.
Does the Manager log all Assets?
Yes = If the Log all Assets setting is enabled, TLC saves the message in the Audit Logger File Store (see What is the Audit Logger?).
No = Otherwise, the Audit Logger ignores the log message.